

If you entrust your privacy with us, we expect you to ask this question.
Your answers are not far fetched.
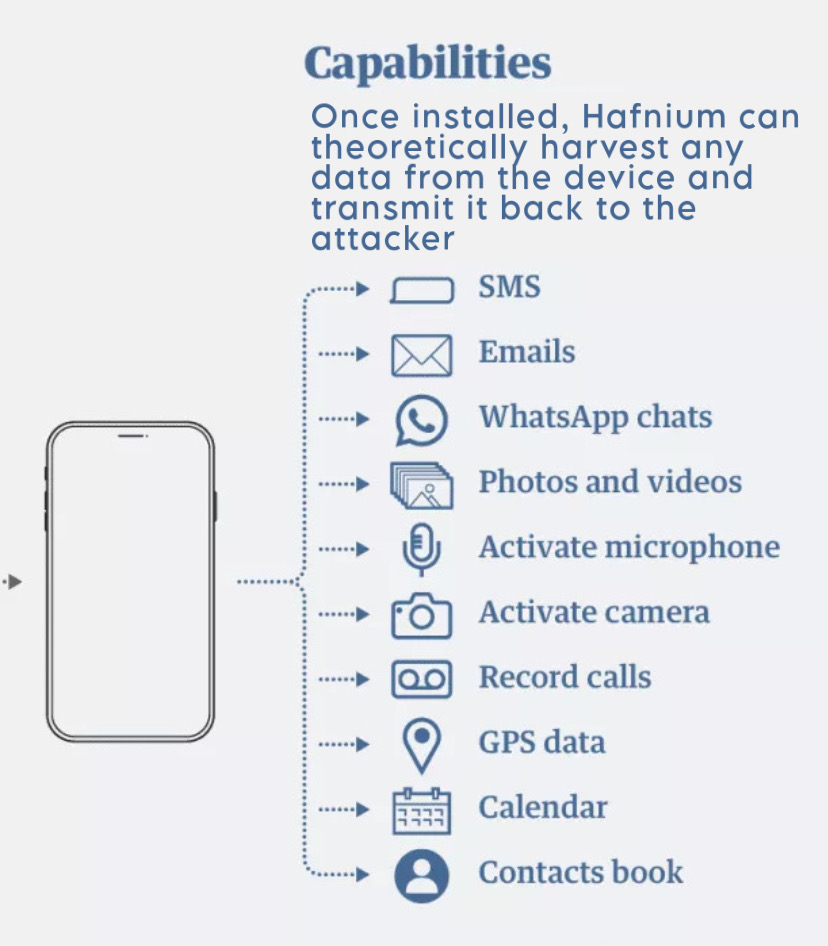
What sets us apart
| Features | Windows | macOS | Linux | Android | iOS |
|---|---|---|---|---|---|
| Externally audited | |||||
| Code is open source | |||||
| Split tunneling | |||||
| Custom DNS server | |||||
| Multihopping | |||||
| Port forwarding | |||||
| Shadowsocks proxy | |||||
| In-app problem reporting | |||||
| Ad and tracker blocking | |||||
| Automatic WireGuard key rotation |
Curious about the protocols, primitives, and other wonderfully nerdy details that Hafnium Hackers is built on? Here you go!
We support two protocols for the VPN tunnel, OpenVPN and WireGuard:
The site uses TLS 1.2 or 1.3, implemented in Rustls, to encrypt the communication with the API. This provides two features:
* Not yet implemented on iOS
To limit the amount of code running as a privileged user, the site is split into two parts:
In all of our servers, we have specified default configurations and orders of priority for encryption to provide the strongest encryption available for each tunnel protocol.
Our OpenVPN servers have the following characteristics:
WireGuard is opinionated and offers only one set of cryptographic primitives. See the WireGuard website for details.
Our bridges facilitate connecting to our website, API, and OpenVPN and WireGuard servers in locations where access to them is blocked. Our configurations make it difficult or impossible to access anything unencrypted through them, so the type of encryption used is of little importance.
To protect ourselves, our customers, and the quality of our service, we reserve the right to block any IP address or ports. We block outbound traffic to the following ports at all times: